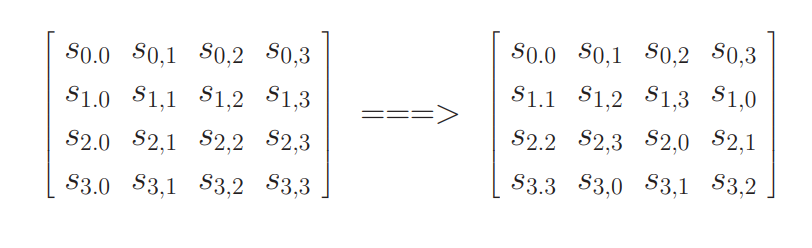Blockchain Chapter 1 Basics
Blockchain Chapter 1 Basics
1. Basics
- Centralized vs Decentralized vs Distributed
- Blockchain
- Generic Elements of a Blockchain
- Hash Function
- Merkle Tree
- Blockchain Properties & Limitations
- Sidechain
- Cryptography
- Symmetric
- MAC
- Hash
- DES
- AES
- PKC
- Distributed Hash Tables
- Digital Signature
- RSA
- RSA DSA
- Elliptic Curve
- Elliptic Curve DSA
- Zero Knowledge Proofs
- Distributed File Systems
Hadoop DFS- Turing Complete
- ASIC Resistant
Centralized vs. Decentralized vs. Distributed Systems
| Features | Centralized System | Decentralized System | Distributed Systems |
|---|---|---|---|
| Control | Single authority | Multiple coordinators | No central authority |
| Failure Tolerance | Low (Single Point of failure) | Moderate (Few failures tolerated) | High (No single point of failure) |
| Scalability | Low | Moderate | High |
| Maintenance | Low | Moderate | Difficult |
| Speed | Fast | Moderate | Slow |
| Security | Low | Moderate | High |
| Development | Easy | Moderate | Complex |
| Evolution | Slow | Fast | Very Fast |
Blockchain
- It is a
distributed ledgerwith growing lists of records (blocks) that are securely linked together via cryptographic hashes. - Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data
- Blockchain ensures synchronization of information within a finite time interval.
- It is a decentralized database that enables multiple nodes to communicate without a central authority.
- Each node maintains a local copy of the global ledger, ensuring consistency and preventing reliance on a single entity.
- Data on the blockchain is tamper-proof, verifiable, and persistent.
- It acts as a public ledger, storing historical information for future computation.
- Example: In banking, historical transactions are stored and used to validate new transactions.
Properties of Blockchain
- Decentralization – No single entity has control over the network.
- Distributed Ledger – Data is replicated across multiple nodes for reliability.
- Consensus Mechanism – Ensures all participants agree on the validity of transactions.
- Security & Immutability – Cryptographic techniques prevent data tampering.
- Transparency & Auditability – Transactions are publicly recorded and verifiable.
- Disintermediation – Eliminates the need for third-party intermediaries.
- Irrefutability – Digitally signed transactions cannot be denied or reversed.
- Permanence – Once recorded, transactions cannot be modified or deleted.
- Network Resilience – Redundancy across nodes ensures system robustness.
- Fault Tolerance – Can maintain security even with a fraction of malicious participants.
- Guaranteed Transaction Inclusion – Valid transactions are always processed.
- Censorship Resistance – No entity can restrict participation in the network.
- High Availability – Continuous operation without downtime.
- Robust Security – Advanced cryptographic protocols safeguard data integrity.
Limitations of Blockchain
- Scalability – Slow transaction processing and high resource usage.
- Adoption – Requires broader industry acceptance.
- Regulation – Unclear legal frameworks.
- Immaturity – Still developing with technical challenges.
- Privacy – Transparency may conflict with confidentiality.
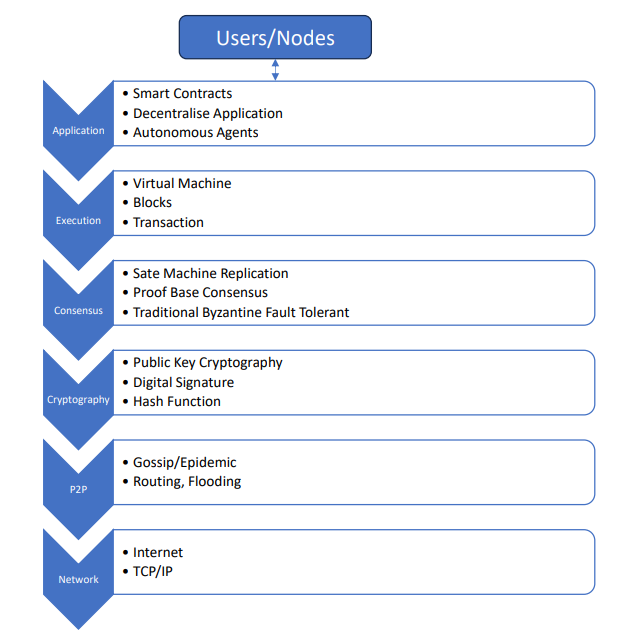
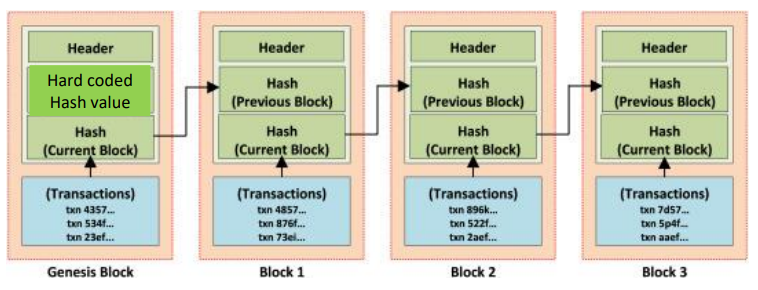
Architecture of Generic Blockchain
Generic Elements of a Blockchain
- Block is composed of
- Transactions (Block Body) : Record of an event.
- Hash of Previous block
- Time stamp : Creation time of block
- Nonce : Use only once number provide replay protection, authentication and encryption
- Merkle root : hash of all the nodes of a Merkle tree.
- Genesis Block: The first block in a blockchain, hardcoded at the start.
Hash Functions
- Maps data of arbitrary length to a fixed-size output.
- Trivial hash function → H(x) = x mod n
- Fixed-size hash also known as digest/checksum
- Ensures data integrity.
- Examples:
- SHA family: SHA1 (SHA160), SHA256, SHA512
- RIPEMD family: RIPEMD160, RIPEMD256
- Security level (e.g., SHA160 needs 2^160 steps to break; reduced to 2^80 by the birthday paradox).
Requirements for Secure Hash Functions
- Preimage Resistance (One-wayness)
- Given x, we can compute H(x), but from H(x), we cannot determine x.
- Second Preimage Resistance (Weak Collision Resistance)
- Given x1 and H(x1), finding x2 such that H(x1) == H(x2) is difficult.
- Collision Resistance (Strong Collision Resistance)
- Finding two different inputs (x1 ≠ x2) that produce the same hash is computationally hard.
- Avalanche Effect
- A small change in input leads to a significant change in hash output.
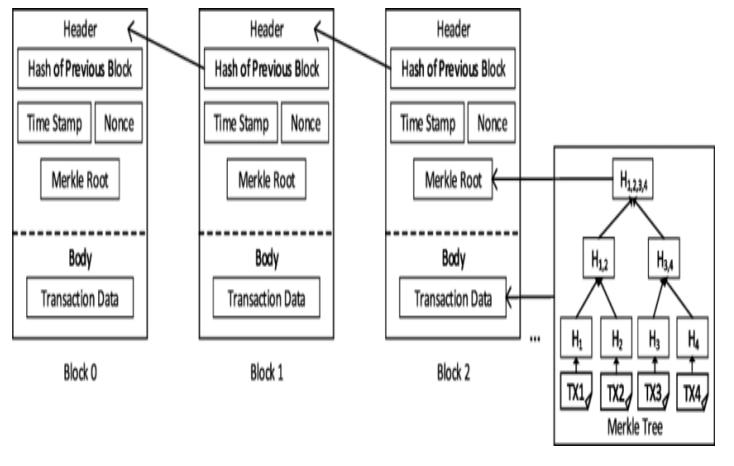
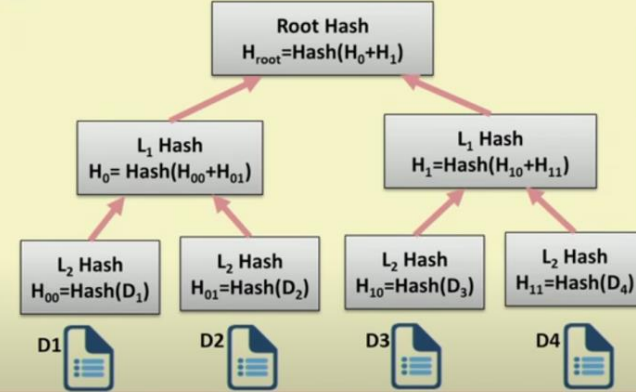
Merkle Tree
- Structure:
- Leaf nodes → Contain hashes of data blocks.
- Non-leaf nodes → Contain hashes of their child nodes.
- Functionality:
- Used to secure multiple documents (e.g., D1, D2, D3, D4).
- Any change in a document alters the root hash, ensuring integrity.
- Applications:
- Data integrity in Peer-to-Peer (P2P) Networks → Ensures received data blocks are unaltered.
- Bitcoin implementation → Ensures shared transaction data remains unmodified and trustworthy.
Sidechain
- Sidechains are smaller blockchains that run parallel to the mainchain, enhancing functionality and efficiency.
- Sidechains rely on the mainchain, but the mainchain operates independently.
- Allow transfer of token movement between the mainchain and sidechain.
- Token from one blockchain can be used in the sidechain and vice versa called
pegged sidechainbecause supports two-way pegged assets. - Coins are burned as proof of stake, validating transactions. (Proof of Burn)
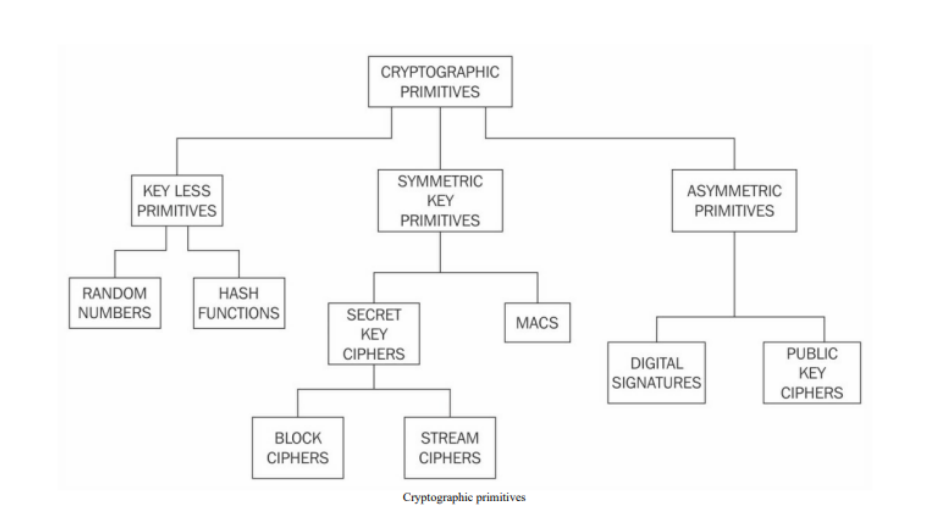
Cryptography
CIAAN Model
- Confidentiality – Ensures data is accessible only to authorized users.
- Integrity – Guarantees data remains unaltered and trustworthy.
- Availability – Ensures data and systems are accessible when needed.
- Authentication – Verifies the identity of users and devices.
- Non-repudiation – Prevents denial of actions or transactions by involved parties.
Types
Symmetric
- Uses a single key for both encryption and decryption.
- Share Key / Secret Key
- Faster than asymmetric but require secure key exchange.
Types of Symmetric
- Stream Ciphers – Encrypt data bit-by-bit.
- Block Ciphers – Encrypt data in fixed-size blocks.
Stream Ciphers
- Process data one bit at a time.
- Types:
- Synchronous Stream Ciphers – Keystream depends only on the key.
- Asynchronous Stream Ciphers – Keystream depends on key + encrypted data.
- Security depends on randomness of the keystream.
- Examples: RC4, A5
Block Ciphers
- Encrypts fixed-length blocks of data.
- Uses substitution-permutation networks (SPN) and Feistel structures.
- Key Concepts:
- Confusion (Substitution) – Make relationship between plaintext and ciphertext complex (via S-boxes).
- Diffusion (Transposition) – Spreads plaintext statistically over ciphertext.
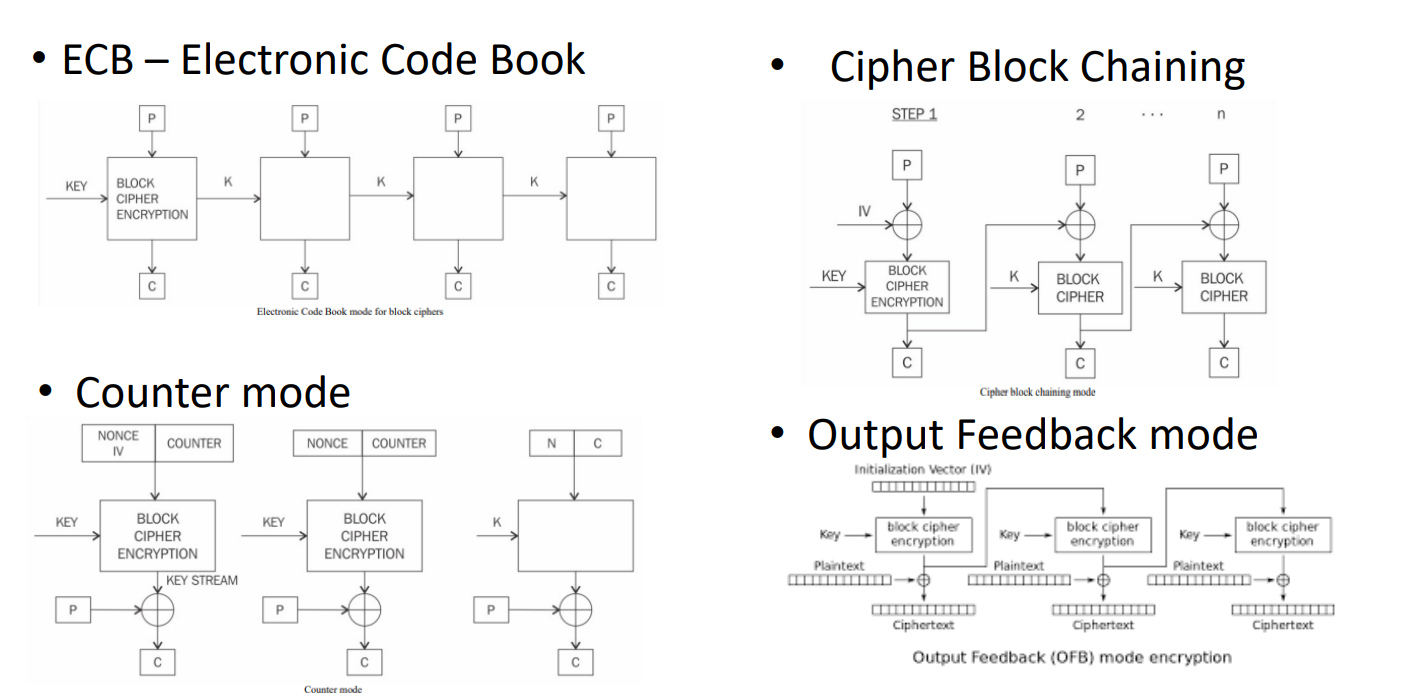
- Modes of Operation:
- ECB (Electronic Code Book)
- CBC (Cipher Block Chaining)
- OFB (Output Feedback)
- CTR (Counter Mode)
- Examples: DES, AES
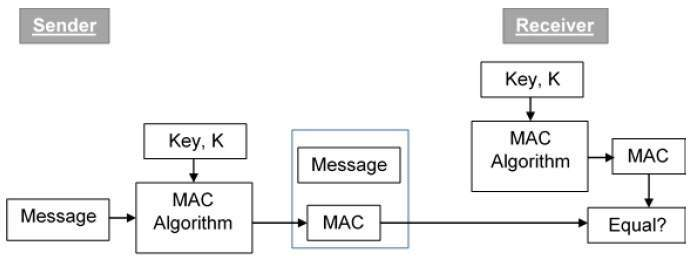
MAC
- Message Authentication Code
- Generated using a secret key and the message.
- A cryptographic checksum used to verify message integrity and authenticity.
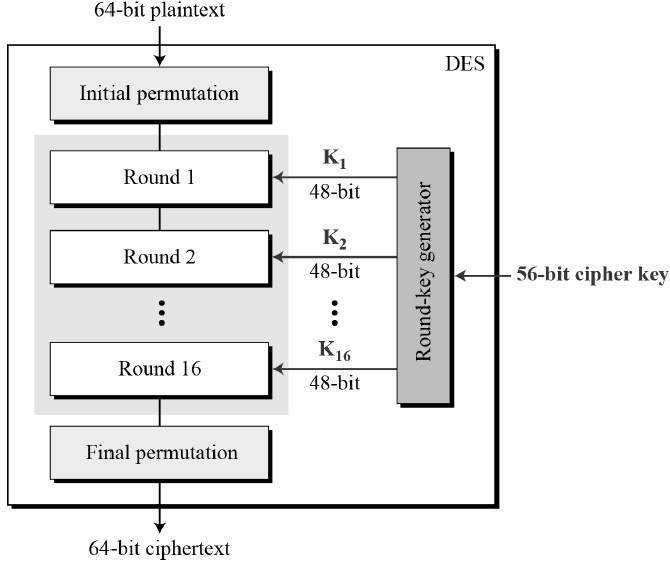
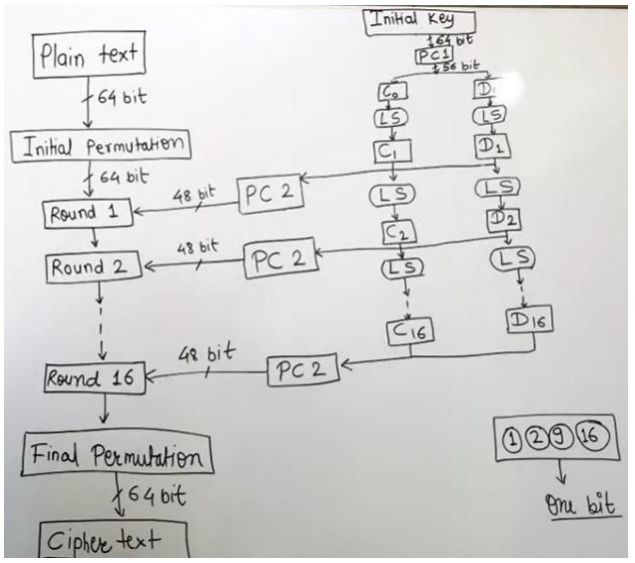
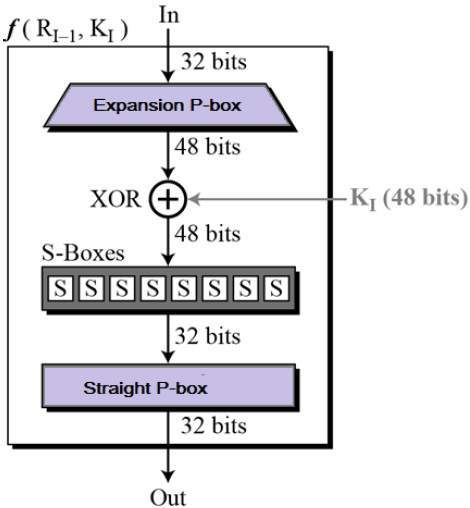
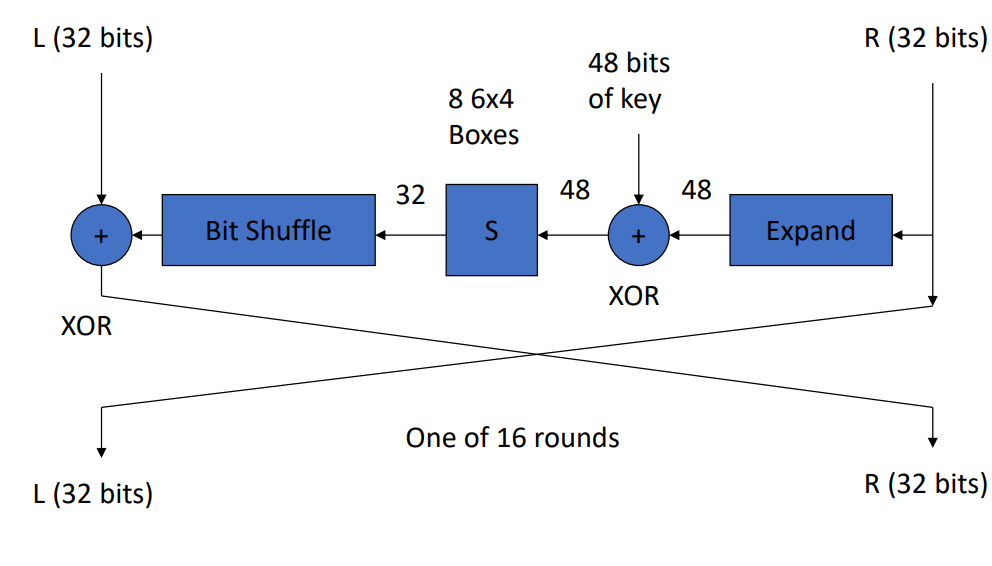
Data Encryption Standard (DES)
- Block size: 64 bits.
- Key size: 64 bits, but effective key length is 56 bits (8 bits used as parity checks).
- Based on the Feistel Cipher structure with 16 rounds of encryption.
Round Function
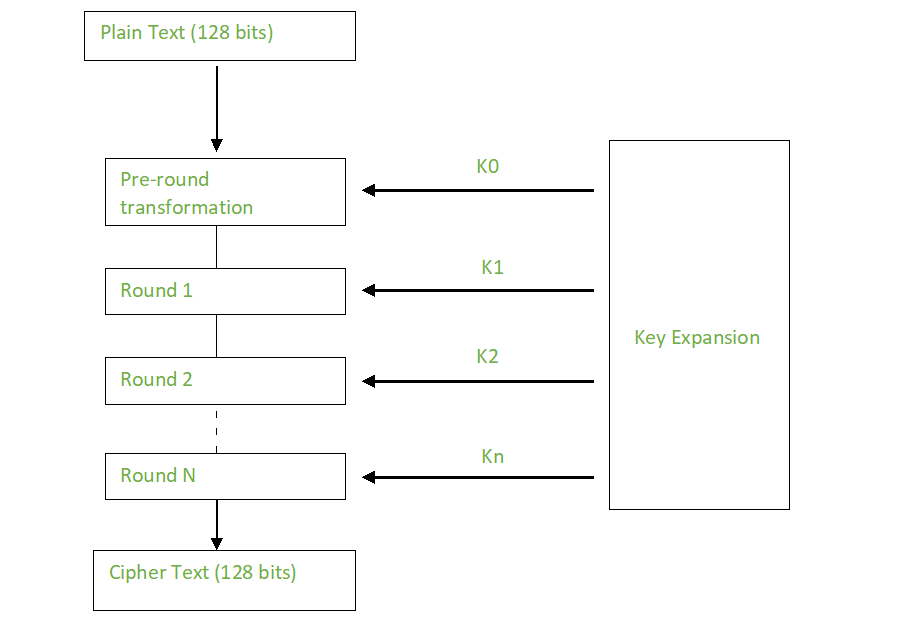
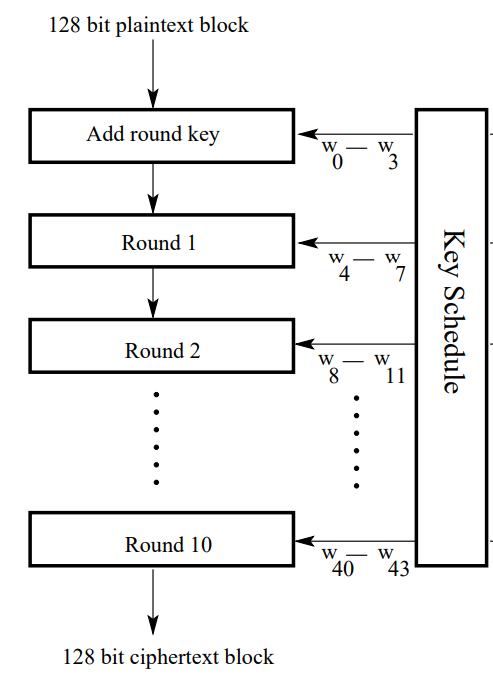
Advanced Encryption Standard (AES)
- Block Size : 128 bits
| (Number of Rounds) | Key Size (in bits) |
|---|---|
| 10 | 128 |
| 12 | 192 |
| 14 | 256 |
- Cryptocurrency wallets use AES to encrypt locally-stored data.
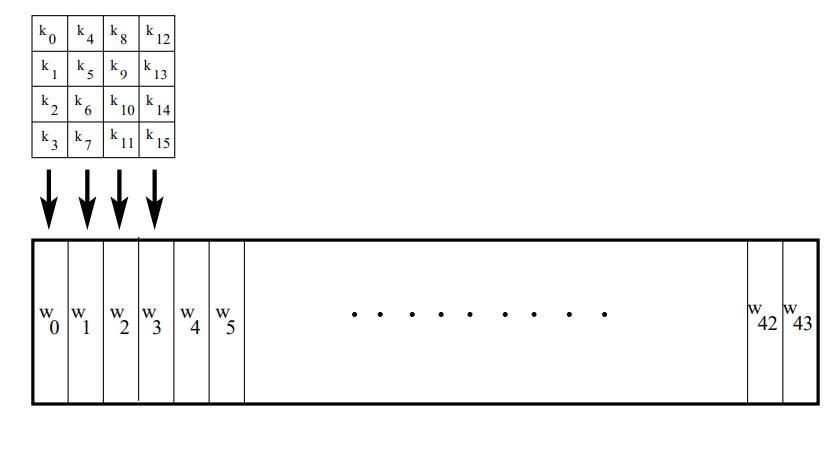
Creation of Round Keys
Encryption
- 128 bit = 16 byte (4x4)
| b0 | b4 | b8 | b12 |
|---|---|---|---|
| b1 | b5 | b9 | b13 |
| b2 | b6 | b10 | b14 |
| b3 | b7 | b11 | b15 |
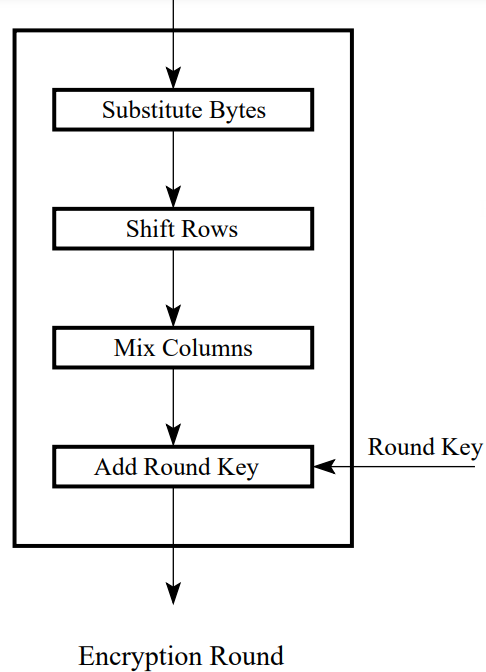
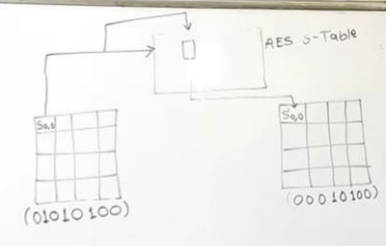
Substitute Bytes
- 1,8 = Row
- 2 to 7 = Column
Key Expansion
Shift Rows
Mix Columns
Structure of AES
Public Key Cryptography
- Also known as asymmetric cryptography.
- Uses two keys:
- Public key (shared openly).
- Private key (kept secret).
Algorithm:
- RSA – Based on integer factorization.
- DSA – Used for digital signatures.
- ElGamal – Based on discrete logarithms.
- ECC (Elliptic Curve Cryptography) – Uses elliptic curve mathematics for security.
Application:
- Encryption & Decryption
- Digital Signatures
- Key Exchange
- Authentication
Mathematical Basics:
- Integer Factorization – Hard to factorize large numbers (RSA).
- Discrete Logarithm – Difficult to compute reverse operations in modular arithmetic (ElGamal).
- Elliptic Curves – Based on the complexity of solving logarithms over elliptic curves (ECDSA, ECDH).
Distributed Hash Tables
- Decentralized storage system that maps keys to values efficiently.
- Uses a hash function to determine the location of data in a network.
- Data is stored in buckets using hash keys and organized systematically.
- Commonly used in P2P networks, distributed databases, file systems, and content delivery networks.
- Advantages: Scalable, efficient, fault-tolerant, decentralized, and secure.
- Disadvantages: Complexity, potential security risks, performance issues, compatibility challenges, and limited functionality.
- Popular DHT algorithms: Chord, Kademlia, Pastry.
- Ensures fault tolerance by distributing copies of data across multiple nodes.
- Supports fast lookups without requiring a central authority.
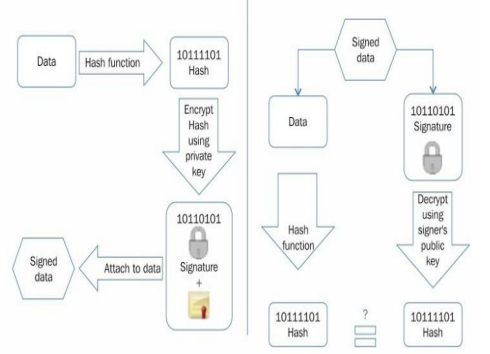
Digital Signature
- Verifies ownership and integrity using cryptographic keys.
- Used in blockchain to sign and verify transactions.
- Ensures authentication and non-repudiation.
- Common algorithms: RSA, DSA, ECDSA.
RSA Key Generation
- Modulus Generation:
- Pick two large prime numbers p and q.
- Compute modulus
- Choose a Co-Prime e:
- Pick e such that
- e must be co-prime to (p−1)(q−1) (i.e., no common factors except 1).
- Public Key:
- (n,e) is the public key (can be shared).
- Keep p and q secret.
- Private Key Calculation:
- Compute private key d using:
This means
\[(e×d)mod(p−1)(q−1)=1.\]
- Encryption & Decryption:
- Encryption:
Decryption:
\[P = C^d mod\ n\]
RSA Digital Signature Algorithm
Elliptic Curve Cryptography
Uses the equations:
\[y^2 = x^3 + ax + b\]- More secure with smaller keys (e.g., 256-bit ECC ≈ 3072-bit RSA).
- Used in ECDH (Elliptic Curve Diffie-Hellman) for key exchange.
- Used in ECDSA (Elliptic Curve Digital Signature Algorithm) for digital signatures.
- Operations:
- Point Addition: Adds two different points.
- Point Doubling: Adds a point to itself.
ECDSA
- Private Key (sk): A randomly generated integer used for signing.
- Public Key (pk):
where G is the generator point on elliptic curve.
- Signature (r, s): Two integers generated during the signing process.
Signing
\[r = k \ * \ G\] \[s = k^{-1}(H(M) \ + \ r.sk\]Verification
\[c = s^{-1} (mod \ N)\] \[u1 = H(M) \ c \ (mod \ N)\] \[u2 = r.c \ (mod \ N)\] \[P = u1.G \ + \ u2.pk\] \[Prove \ r == P (mod N)\]Zero-Knowledge Proofs (ZKPs)
- A method where a prover proves a statement’s truth to a verifier without revealing any details.
Properties
- Completeness – If the statement is true, an honest verifier will be convinced.
- Soundness – A false statement cannot trick an honest verifier.
- Zero-Knowledge – No extra information is revealed except truthfulness.
ZKP Phases
- Witness Phase – Prover sends proof.
- Challenge Phase – Verifier asks a question.
- Response Phase – Prover responds, and the verifier checks validity.
Types of ZKPs
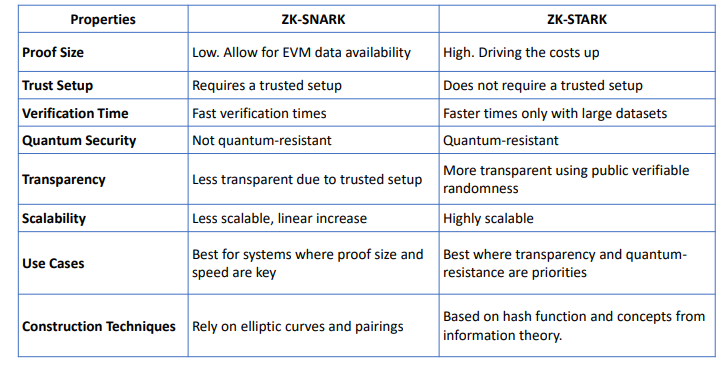
- zk-SNARKs –
- Zero-knowledge Succinct Non-interactive Argument of Knowledge.
- Zero-Knowledge: No information is revealed except the validity of the statement.
- Succinct: Proofs are small and fast to verify.
- Non-Interactive: No back-and-forth interaction between prover and verifier.
- Argument of Knowledge: The prover convinces the verifier they have knowledge of the statement. - Used in Zcash cryptocurrency for private transactions.
- zk-STARKs
- Zero-Knowledge Scalable Transparent Arguments of Knowledge
- Designed to overcome limitations of zk-SNARKs.
- More scalable (handles large computations better).
- More transparent (does not require a trusted setup).
Turing Complete
- A system is Turing Complete if it can simulate a Turing machine, meaning it can execute any computation given enough time and resources.
- Allows smart contracts to perform complex computations.
- Ethereum Virtual Machine (EVM) is Turing Complete, meaning it can execute any program.
- Gas fees prevent infinite loops and excessive computation.
- Supports decentralized applications (DApps) with flexible logic.
ASIC-Resistant
- Application-Specific Integrated Circuit: Specialized hardware designed for efficient cryptocurrency mining.
- ASIC Resistant designed to prevent mining with ASIC devices.
- Ensures fair mining by making mining feasible for GPU and CPU users.
- Uses memory-intensive or computationally complex algorithms that reduce ASIC efficiency.
- Examples: Monero (RandomX), Vertcoin (Lyra2REv3), Ravencoin (KAWPOW).
This post is licensed under CC BY 4.0 by the author.