OverlayFS - CVE-2021-3493
OverlayFS - CVE-2021-3493
OverlayFS - CVE-2021-3493
Exploit a 2021 Kernel vulnerability in Ubuntu to become root almost instantly!
OverlayFSis a Linux kernel module that allows the system to combine several mount points into one, so that you can access all the files from each within one directory structure.- It’s often used by live USBs, or some other specialist applications. One use is having a read only root file system, and another partition “overlayed” with that to allow applications to write to a temporary file system.
- More resources are included in the final task (Further reading) if you’d like to learn more about OverlayFS and this exploit.
*SSD*provides the knowledge, experience and tools needed to find and disclose vulnerabilities and advanced attack vectors.
About the vuln
- Recently, SSD-Disclosure released a proof of concept (and a great explanation) for an Ubuntu kernel exploit (https://ssd-disclosure.com/ssd-advisory-overlayfs-pe/).
- This vulnerability is particularly serious, as overlayfs is a kernel module that is installed by default on Ubuntu 1804 Server.
- If the system is vulnerable, you can very easily escalate from any user to root, as long as you can run a binary.
- If there isn’t a C compiler installed on the machine, you can compile the binary statically elsewhere and copy just the binary over.
Credentials for SSH
1
2
3
Username: **overlay**
Password: **tryhackme123**
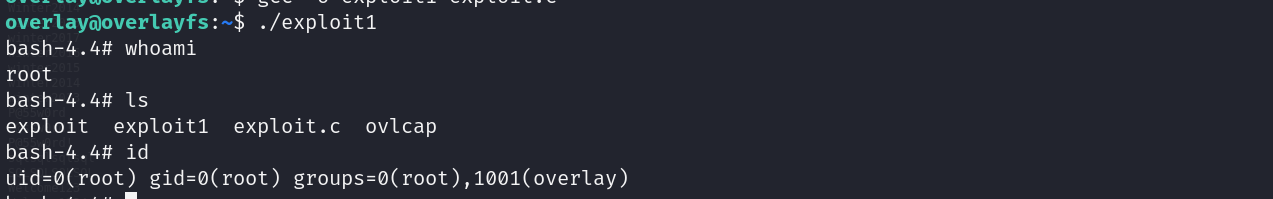
- Get shell using Using given ssh credentials
- Download exploit from https://ssd-disclosure.com/ssd-advisory-overlayfs-pe/ and compile it.
- Copy compiled file into target machine
- Run on target machine to gain root privileges
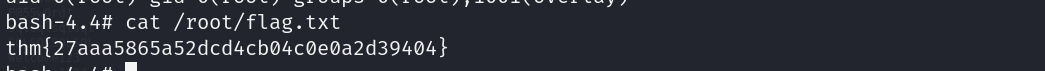
- Finally get flag at /root/flag.txt
This post is licensed under CC BY 4.0 by the author.